In today’s digital landscape, safeguarding our devices from harmful software has become increasingly crucial. Understanding how to effectively eliminate unwanted programs can help maintain the integrity of your system and protect your personal information. This section will provide valuable insights into tackling these threats independently, ensuring your computer remains functional and secure.
To successfully address the presence of harmful applications, it is essential to follow a systematic approach. This involves identifying the offending software, assessing its impact on your device, and employing strategic methods to terminate it. With the right techniques, you can restore your system to its optimal state and enhance its resilience against future attacks.
Throughout this guide, we will explore various tactics to help you navigate the complexities of dealing with these unwanted intrusions. By arming yourself with knowledge and employing effective strategies, you can regain control over your device and enjoy a safer computing experience. Embracing proactive measures will not only aid in resolving current issues but also fortify your system against potential threats.
Understanding Manual Virus Removal
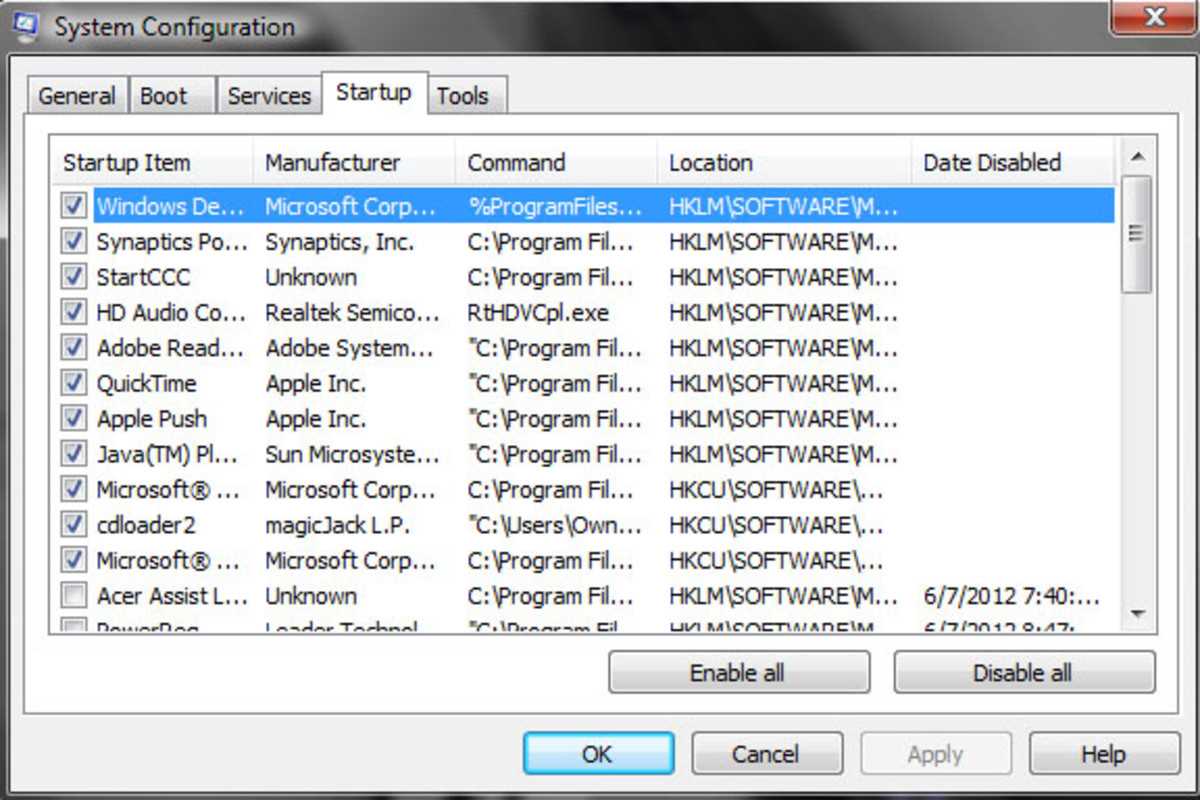
This section provides insight into the process of eliminating unwanted software threats from your system without relying on automated tools. The focus lies on identifying malicious entities and systematically eradicating them to restore your computer’s functionality and security.
When dealing with unwanted programs, the initial step involves recognizing their presence and understanding their behavior. This can often require keen observation of system performance and unusual activity that may signal an intrusion. Armed with knowledge, users can embark on the task of cleansing their devices effectively.
Following identification, it is crucial to establish a strategic approach for addressing the issue. This typically includes accessing various system locations where harmful software may reside and taking appropriate measures to eliminate them. Below is a table summarizing key steps involved in this process:
| Step | Description |
|---|---|
| 1 | Identify unusual behavior or performance issues. |
| 2 | Locate and access control panels or file directories. |
| 3 | Uninstall or delete suspicious applications and files. |
| 4 | Scan for additional threats using trusted software. |
| 5 | Restore system settings to ensure optimal performance. |
In conclusion, the process of cleansing a device of malicious entities requires a methodical and informed approach. With the right knowledge and tools, users can effectively protect their systems and maintain a secure digital environment.
Common Symptoms of Virus Infection
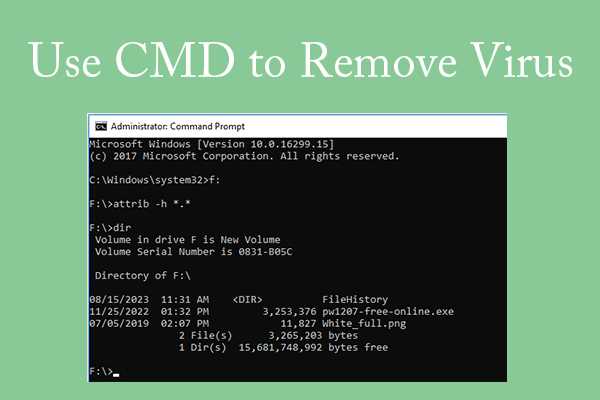
Recognizing the signs of a digital infection is crucial for maintaining system integrity. Various indicators can suggest that a device may be compromised, leading to potential data loss or unauthorized access. Awareness of these symptoms can help users take prompt action to safeguard their information.
Slow Performance: A noticeable decrease in speed is often one of the first signs. Programs may take longer to load, and overall system responsiveness may decline, making everyday tasks frustrating.
Frequent Crashes: Unexpected shutdowns or crashes of applications can signal underlying issues. If your device starts freezing or rebooting without reason, it’s essential to investigate further.
Unusual Pop-ups: An increase in intrusive advertisements or unexpected pop-up windows can indicate a compromised system. These may appear even when not browsing the internet, often serving unwanted content.
Unexplained Data Usage: Sudden spikes in data consumption without any change in usage patterns can suggest that unauthorized applications are transmitting information. Monitoring data usage can help identify suspicious activity.
Changes in Settings: If you notice alterations in system settings, such as altered homepage or search engine preferences, it may be a sign of an unwanted intrusion. Keeping an eye on these changes is important for maintaining control over your device.
Missing Files: The disappearance of documents or programs can be alarming. If files vanish or become inaccessible, it may be indicative of a more serious underlying issue that needs addressing.
Essential Tools for Removal Process
In the quest to eliminate unwanted software from your system, having the right resources at your disposal is crucial. These tools not only enhance the efficiency of the task but also ensure a thorough and effective cleansing of your device. By equipping yourself with the necessary applications, you can confidently tackle various threats and safeguard your digital environment.
Antivirus Software: This type of application serves as the first line of defense against harmful programs. It scans your system for potential threats and provides options for quarantine or deletion. Regular updates are essential to keep the software effective against new forms of malware.
Malware Removal Tools: These specialized utilities focus specifically on identifying and eliminating malicious software that traditional antivirus solutions might miss. They often feature deep scanning capabilities and real-time protection to enhance your system’s security.
System Restore Points: Creating restore points allows users to revert their systems to a previous state before any unwanted programs were installed. This tool acts as a safety net, providing peace of mind during the cleaning process.
Safe Mode: Booting your system in this mode limits the operation of non-essential applications and services, making it easier to identify and eliminate stubborn threats. This environment provides a controlled setting for addressing problems without interference from other software.
Backup Solutions: Regularly backing up important files ensures that you do not lose valuable data during the cleansing process. Utilizing cloud storage or external drives can provide a secure way to store your information and recover it if necessary.
With these essential tools, you are well-equipped to address any unwanted software issues effectively. Each resource plays a vital role in maintaining the integrity of your system and ensuring a safe digital experience.
Step-by-Step Removal Instructions
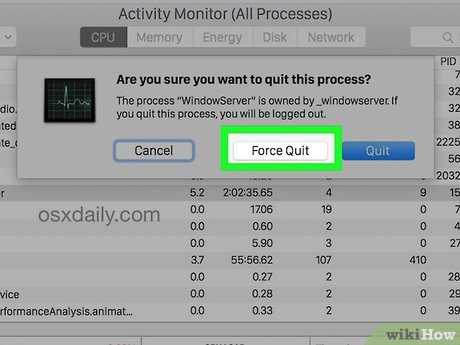
This section provides a comprehensive guide to eliminating unwanted software from your computer system. Following these systematic steps will help ensure that any malicious elements are effectively dealt with, restoring your device to its optimal state. Adhering to the outlined process is crucial for achieving the desired outcome.
Preparation Steps
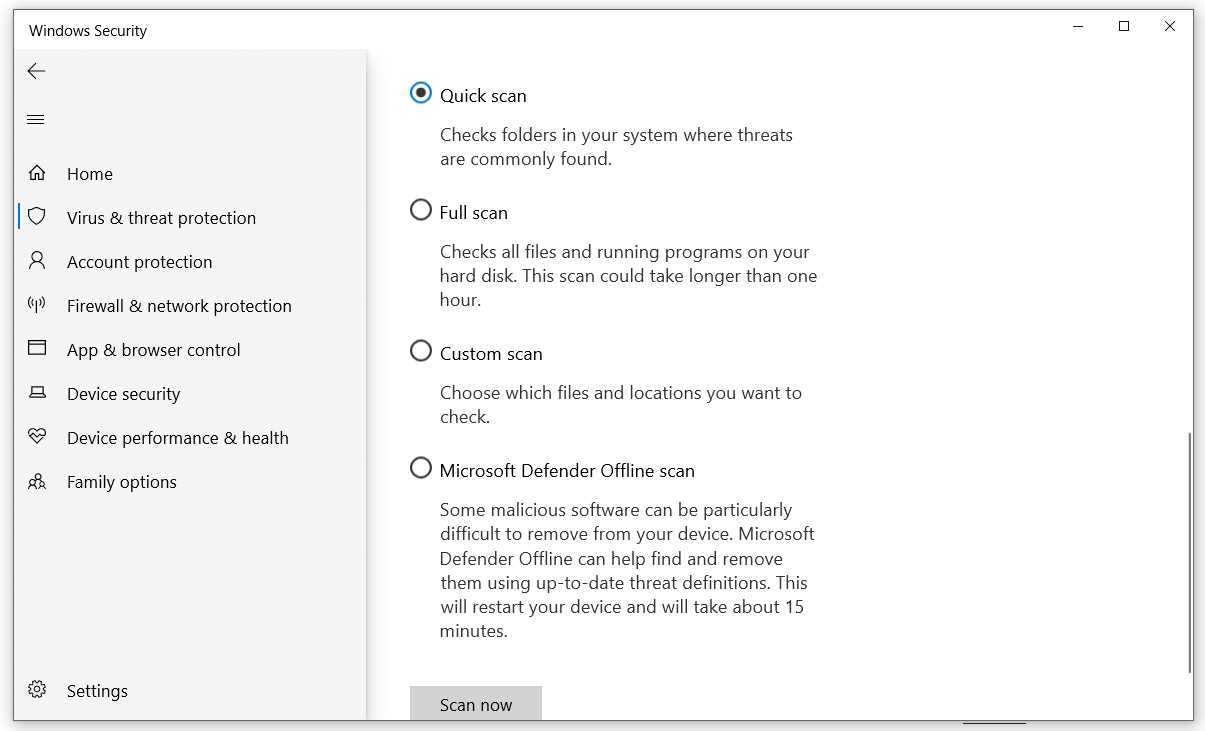
- Backup important files to an external drive or cloud storage.
- Disconnect from the internet to prevent further issues.
- Gather necessary tools, such as antivirus software or a malware scanner.
Execution Steps
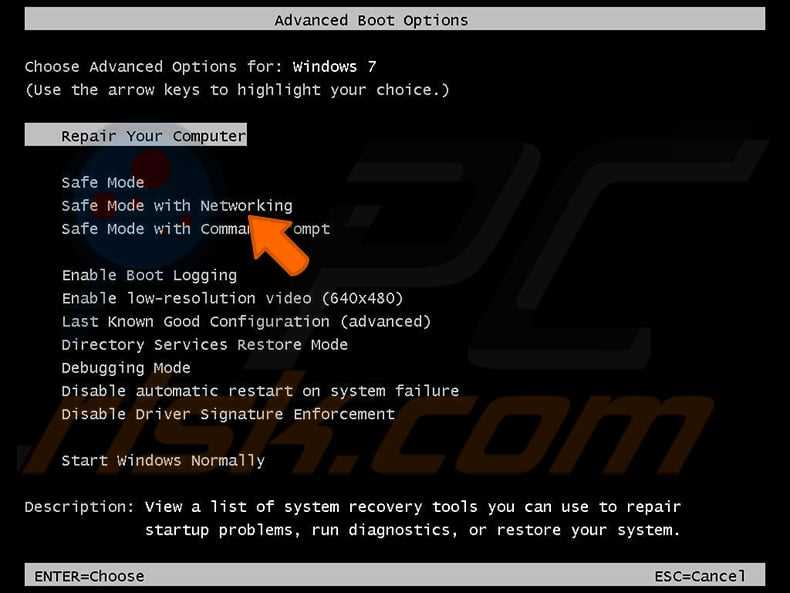
- Restart your computer in Safe Mode:
- For Windows: Press F8 during startup and select Safe Mode.
- For Mac: Hold the Shift key while booting up.
- Run the antivirus or malware scanner to identify problematic software.
- Follow the prompts to eliminate any identified threats.
- Delete any suspicious applications from your system:
- For Windows: Go to Control Panel > Programs > Uninstall a program.
- For Mac: Open Finder > Applications and drag unwanted apps to the Trash.
- Clear temporary files and browser caches to ensure complete elimination.
- Restart your device normally and monitor for any unusual behavior.
By following these structured steps, you can effectively cleanse your system of harmful software and enhance its overall performance.
Safe Browsing Practices to Prevent Viruses

Adopting secure browsing habits is essential in today’s digital landscape. By being vigilant and informed, users can significantly reduce the risk of encountering malicious software. Simple yet effective measures can protect personal information and enhance overall online safety.
1. Keep Software Updated: Regular updates to your operating system, web browser, and applications help patch vulnerabilities that could be exploited. Always enable automatic updates whenever possible to ensure you receive the latest security features.
2. Use Reputable Security Software: Employ trusted security solutions to provide real-time protection against potential threats. These tools can detect and neutralize harmful elements before they cause harm.
3. Be Cautious with Downloads: Avoid downloading files or software from unverified sources. Always verify the authenticity of websites and only download content from reputable platforms.
4. Practice URL Awareness: Before clicking on links, hover over them to preview the destination. Ensure the URL is spelled correctly and starts with “https://” to confirm a secure connection.
5. Enable Pop-Up Blockers: Utilizing pop-up blockers can prevent unwanted ads and potentially harmful scripts from running. This measure adds an extra layer of protection while browsing.
6. Educate Yourself about Phishing: Familiarize yourself with common phishing tactics. Be skeptical of unsolicited emails or messages requesting personal information, and always verify the sender’s identity.
7. Use Strong Passwords: Create complex passwords that combine letters, numbers, and special characters. Change passwords regularly and consider using a password manager to keep them secure.
8. Limit Personal Information Sharing: Be mindful of the information you share online. Review privacy settings on social media platforms to control who can access your personal data.
By implementing these practices, individuals can create a safer online environment and significantly decrease the likelihood of encountering harmful software.
Identifying Suspicious Programs on Your System

Detecting unwanted applications on your computer is crucial for maintaining its health and security. These programs can negatively impact system performance and compromise your data integrity. Recognizing the signs of potentially harmful software is the first step in safeguarding your digital environment.
Signs of Unwanted Applications
One of the key indicators of suspicious software is unusual system behavior. This may include unexpected crashes, sluggish performance, or frequent pop-up ads. Additionally, if you notice unfamiliar programs starting automatically during boot-up, it’s worth investigating further. Regularly reviewing installed applications can help you identify any that you do not remember installing.
Analyzing Running Processes
Another effective method for identifying dubious applications is by examining the processes running on your system. Use the Task Manager (Windows) or Activity Monitor (Mac) to view active programs. Pay close attention to any unfamiliar names or high resource usage that seems out of place. Researching these processes online can provide insight into their legitimacy and potential risks.
Stay vigilant and maintain a proactive approach to protecting your system. By regularly monitoring installed software and running processes, you can minimize the risk of harmful applications affecting your computer’s performance.
When to Seek Professional Help
In certain situations, addressing computer security issues on your own may not be sufficient. While basic troubleshooting can resolve minor complications, there are circumstances where the intervention of an expert is advisable. Understanding these scenarios can save time, effort, and potential data loss.
Firstly, if you encounter persistent complications that resist your attempts at resolution, it may be a signal to consult a specialist. Ongoing issues can indicate deeper problems that require advanced techniques and tools. Additionally, if your device exhibits unusual behavior–such as unexpected crashes, performance slowdowns, or unfamiliar applications–professional assistance may be warranted to ensure your system’s integrity.
Moreover, in cases where sensitive information is at risk, such as personal data or financial details, seeking help from a trained technician can provide peace of mind. Experts possess the knowledge to address potential threats effectively, minimizing the risk of data breaches.
Lastly, if you lack the technical expertise or confidence to proceed, it is always wise to reach out for professional support. Attempting complex procedures without the necessary skills can lead to further complications, making it essential to rely on knowledgeable individuals who can provide the expertise needed for a thorough resolution.